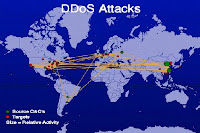
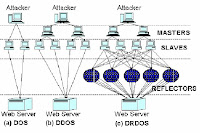
Nowadays, e-auction becomes a normal and popular internet activity for the internet users. However, e-auction fraud such as bid shielding, shilling, failure to ship merchandise and other problems still exist.
Thus, some important issue must take note when a consumer participating in an e-auction in order to minimize or prevent e-auction fraud.
User identifies verification: IC number, mother’s name, driver’s license or such privacy information can use by users to identify the verification when make bid in e-auction or trading in the internet.

Authentication service: It is a service provide by the specific companies use to determine whether an item is genuine or not. However, sometimes different expert authenticators may have different opinion when doing the verification in the same item based on their different experience.
Grading services: It used to determine the physical condition of the items. Different items may have different grading system. Thus, it will be more precise when grading the items.
Escrow Service: It provides users with safe and convenient environment when

they conduct business with other users through internet. Escrow service provider act as a third-party. They collect, hold and send a buyer’s money to a seller according to instructions agreed on by both buyer and seller. Once the buyer receives and approves the item from the seller within an agreed time frame, the escrow service will send the payment to the seller.
Feedback forum: Feedback forum is a good platform that allows buyer and sellers to build up their own e-auction reputation. Users can give comment on their online trading experience. It is especially useful when potential buyer make reference to those comments in the feedback forum in order to make online trading decision.
Non-payment Punishment: It is a policy implemented by the e-Bay to punish those who do not pay for their winning bids at the due time. For example, suspension of their accounts. This can be a warning to those bidders who do not honor in the winning bids.

 Other than convenient, I am emphasis on the security when I trade. There is a safetrade service in this website that provide the buyer and seller to complete their online transaction more safety. Furthermore, people that are currently not residing in Malaysia are not allowed to sell things over this website. This is because they want to reduce and prevent online fraud. With this service provided, it enhances users confident during the online transaction.
Other than convenient, I am emphasis on the security when I trade. There is a safetrade service in this website that provide the buyer and seller to complete their online transaction more safety. Furthermore, people that are currently not residing in Malaysia are not allowed to sell things over this website. This is because they want to reduce and prevent online fraud. With this service provided, it enhances users confident during the online transaction. 





 Nowadays, e-tailing take part in pure play-type business have the opportunity to gain higher profit margins because the overhead expenses associated with a physical retail space, such as retail space, labour and inventory is significantly alleviated. Pure play allows a retailer to reach customers world wide while they still maintaining in one location for each customer to visit. It is operate for 24 hours a day and 7 days a week.
Nowadays, e-tailing take part in pure play-type business have the opportunity to gain higher profit margins because the overhead expenses associated with a physical retail space, such as retail space, labour and inventory is significantly alleviated. Pure play allows a retailer to reach customers world wide while they still maintaining in one location for each customer to visit. It is operate for 24 hours a day and 7 days a week.