 Distributed denial-of-service (DDoS) can become a useful tool by the legitimate firms to damage their competitors’ website or servers. However, it only take place in internet.
Distributed denial-of-service (DDoS) can become a useful tool by the legitimate firms to damage their competitors’ website or servers. However, it only take place in internet.
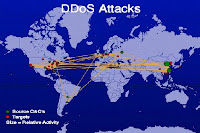
 DDoS attack is an attempt that attacker gain the illegal administrative access to as large amount of compromised systems on the internet as possible to attack a single target. It purposes is to make the computer resource unavailable to its intended users or potential users. The common method of DDoS attack involves the flood of incoming messages to the target systems with external communications requests. Thus, the target system cannot respond to legitimate requests as soon as possible or cannot responds to the valid applications effectively and efficiency.
DDoS attack is an attempt that attacker gain the illegal administrative access to as large amount of compromised systems on the internet as possible to attack a single target. It purposes is to make the computer resource unavailable to its intended users or potential users. The common method of DDoS attack involves the flood of incoming messages to the target systems with external communications requests. Thus, the target system cannot respond to legitimate requests as soon as possible or cannot responds to the valid applications effectively and efficiency.
Normally, the DDoS attack will force the targeted system to reset or close down for few hours even for few days in order to repairs and restore. This is because DDoS attack will consume all the resources of the targeted system that it can no longer provide its intended services or as a communication media between the users and the targeted system.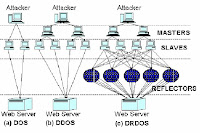 DDoS attack always used in the business industry on the internet. This attack will seriously influence the operating of the competitors’ computer system especially those websites that major revenue is rely on the online selling or transaction fees. Once the website closes down for few hours or few days, the million in dollar per day will be loss. Furthermore, reputation of the company and the confident of the users will loss due to the DDoS attack to the company system. Thus, most of the companies are afraid to become the target system of DDoS.
DDoS attack always used in the business industry on the internet. This attack will seriously influence the operating of the competitors’ computer system especially those websites that major revenue is rely on the online selling or transaction fees. Once the website closes down for few hours or few days, the million in dollar per day will be loss. Furthermore, reputation of the company and the confident of the users will loss due to the DDoS attack to the company system. Thus, most of the companies are afraid to become the target system of DDoS.









